Many in the business and academic communities have been up in arms that security risks are too high in cloud implementations, and therefore the status quo is better for sensitive government and commercial environments. Many of those same individuals and organizations are pursuing research grants to come up with new and revolutionary ways to meet this “menacing challenge.” Others joining the chorus have significant investment and long-term contracts to exploit and continue to profit from the status quo. In reality, the issues – when viewed clearly – are the same for a cloud-hosted environment or any well-managed bespoke data center. Let’s delve into the fundamentals that we have known for decades to address the security questions about cloud deployments; they are the fundamental technical solutions we often ignore or forget in our rush to pursue the “latest and greatest.”
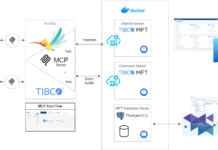
Let’s begin by asking: “What do you know about your cloud provider?” What certifications, evaluations and practices define them? From Amazon Web Services (which has nearly every certification from PCI and FIPS and FISMA to FedRAMP) to your favorite legacy systems integrator, (who has some subset of the measures of trustworthiness) you need to know why they are adequate and appropriate to your information and mission. While the mentioned certifications are mostly for targeted environments, they are very significant to how much you as an end-customer can trust their environment and processes.
When cloud became a rallying cry for efficiency in enterprise and government, every legacy systems integrator and outsource host suddenly redefined themselves as cloud providers. This isn’t necessarily a bad thing, but you should understand how your cloud partner thinks, acts and most importantly, how it accepts accountability for your information.
The level of assurance you need is tied to the sensitivity and value of the information your applications or their cloud applications are processing on your behalf. If you are moving your marketing information and related processing to their cloud, you only need to understand the availability, accessibility and integrity measures your partner is providing. As long as they deliver your information against a reasonable service level agreement and assure you that the information delivered is unaltered, that’s all that you need from them. You don’t need to know about their ownership, employees, certifications and detailed security practices. You don’t care who sees the information because its purpose is to be seen. You just want to ensure that as many people as possible have access to it.
When you process sensitive information on your friendly cloud partner, you need to know who they are, who owns or influences them, who their employees are and that you can trust them as much as your own employees. You also need a clear understanding of their physical and technical security investments, as well as how often they test and evaluate all of the above. Processing your, trade secrets, and proprietary, financial or classified information requires a whole other level of knowledge, but does not necessarily exclude any selected partner as long as they are trustworthy enough. Trustworthiness at this level can mean background investigations on not only employees with access to your information, but for executives and influencers like board members or significant investors. Beyond knowing who runs your cloud, a lot of technical issues impact their level of trustworthiness. Stay tuned for more discussions about physical protections and their limitations.